Do you want to know how to secure a website to keep yours safe from hackers? Or looking for ways to increase website security? You’ve come to the right page.
Being a website owner, there isn’t anything more terrifying than someone stealing your data or altering your files. In this age of the internet, you need to secure your website because attacks on your website may also cause you to lose your personal data.
In this article, we’re going to go over each, and everything that you need to know to make your website secure. This is a definitive security guide so sit back and read on to know more.
What is Website Security and Why Do You Need It?
Before we jump right into the ways of making your website secure, you must understand a couple of things first. With the internet taking over the world, your website can be easily compromised. So, let’s go through what website security is.

Security is a continuous process. Just because you applied some security principles doesn’t make you fully secure. You’ll need to continuously update things and switch to new security measures.
Burglars will find new and innovative ways to break into your house. You could lock every door and window and they’d still get in if they really want to. It’s the same with your website.
Website security is the measures taken to secure your website from cyberattacks, which is an attempt to disable computers or steal data through the internet. It’s an essential part of managing a website. Since the cyber world is ever-evolving, security should too.
If you want to learn about securing your online store, then check our guide on eCommerce security.
Why Do Websites Get Hacked?
The next part you need to understand is why websites get hacked. You could say that your website is a relatively smaller one and doesn’t have a lot of data. But that doesn’t mean hackers disregard your website. So, let’s look into why websites get hacked.

- A lot of reasons to hack a website nowadays are just for fun. Hackers will disrupt anyone’s data they can find.
- Another reason may be for money. Hackers sabotage a website, change the admin details, and blackmail you for money.
- Another common reason is personal disputes. Did you know that you can hire hackers to disrupt a rival company’s business? A lot of people do this around the world.
According to Cybersecurity Ventures, cybercrime is more profitable than the global illegal drug trade.
Hackers could also break into your website to exploit your visitors and potentially gain money from them illegally. They could also hack your website to steal information stored in the server or to abuse server resources and make you pay for it.
Cyberattacks have become so large in the past few years that one vulnerability can end an entire company if someone chooses to hack it. According to Security Today, 67% of businesses attacked by hackers weren’t confident they could recover in 2023. [1]

Even the bad guys, also known as black hat hackers, have openly claimed that traditional firewalls and anti-virus are irrelevant nowadays. But, by applying some basic security, you can prevent most of the weak breaches.
Common Website Vulnerabilities and Threats
Vulnerabilities are flaws in your website that can be exploited to gain access. To know how you can secure your website, you must first know what can compromise your website. Here are some common website vulnerabilities that can compromise your website.

i. Cross-Site Scripting (XSS)
XSS attacks are carried out by hackers injecting malicious client-side codes into your website and using it to spread the code. This usually affects your audience as their browsers are forced to run the hacker’s malicious code.
This could seriously harm your reputation as the hacker’s code could be anything. Sometimes, it could be something your website host’s terms and conditions don’t allow. That could lead to the deletion of your website.
Not only are your audience in danger, but you are also too. If you log in as a site administrator, the malicious code could take over your website using admin privileges.
ii. Structured Query Language (SQL) Injection
SQL injection is a technique used to inject malicious code into an existing SQL statement. This type of attack is carried out by a hacker modifying requests sent by your website to its database and gaining access to information.
SQL injections are usually done through one of your website’s pages where there is a text input feature. Search boxes and form fields are commonly used for SQL injections.
In some cases, the hacker might have an automated program for SQL injection that doesn’t specifically require the text input field. All they need to do is provide your website’s URL and the program can inject from any part of your website.
What’s scary about this attack is that hackers gain access to your database. Which means they now have all your customers’ private information. The hacker can then dump the data online and ruin your reputation.
iii. Distributed Denial of Service (DDoS)
DDoS attacks are non-intrusive attacks. What this means is that they don’t rely on the website to execute. DDoS attacks are typically carried out by a hacker sending a lot of requests to the server in order to crash it.
DDoS attacks are always done without your website being involved so it’s a scary one. They work by flooding your website with requests more than the server can handle. This causes websites to crash.
And if you have a vulnerable endpoint, even less traffic is enough to crash your website. This type of attack causes your business to go down.
iv. Brute Force Attacks
One of the most common types of attacks is the brute force attack. As it sounds, this type of attack is carried out by forcing your website to give admin access through various means.
According to Cybersecurity Ventures, brute force attacks affect one in ten websites in the US every day. Brute force is carried out by a hacker running a malicious script. The script contains every letter and symbol in every language.

The script then runs over and over until it finds out the correct combination of letters or numbers to your admin details. This type of attack takes a long time to execute and you can see a lot of requests to your admin panel. So, you know a brute force attack is coming.
Brute force attacks are very effective against weak passwords. We’ll talk about dealing with this further in the article.
v. Malware Attack
Malware attack is the injection of malicious files on a website to maintain admin access. This type of attack is usually a second wave to any other attack.

A malware attack can only affect compromised websites. So, after your website has been compromised with any of the above attacks, hackers can infect your website with malware.
Did you know?
- In 2023, there were approximately 6.06 billion malware attacks worldwide, marking a 10% increase from the previous year. [2]
- As of Q1 2024, AdWare accounted for 46.16% of detected mobile malware globally, followed by RiskTool at over 21%. [3]
- The number of ransomware attempts worldwide has been significant, with millions of attempts recorded annually. [4]
Malware can range from keyloggers, which record every keystroke you perform, to screen viewers, which lets a hacker view what you’re doing on your screen. This way, they know your password even if you’ve already changed it.
They can also affect your audience. If your audience isn’t aware, their computers can become a part of a botnet. A botnet is a collection of computers infected by the same malware that a hacker can use to control all of them.
This is pretty scary, so we’ll talk about how to combat malware attacks very soon.
vi. Phishing
Phishing is the act of tricking people to give out their personal data. This type of attack is usually detectable.
A hacker can carry out this type of attack by replicating your website and tricking your audience to enter their personal details on the fake website. The fake website then redirects the data to the hacker’s computer.
People with little to no technical knowledge are very vulnerable to this type of attack. Hackers will make use of your employees or the audience to disrupt your website.
This is a very common attack and can be combated easily through some technical training. We’ll talk in detail about how to combat this type of attack later in this article.
Now that we know some basic security vulnerabilities and what they do, let’s talk about your website’s security framework. How security works on your website and how you can modify some parts of your website to make it more secure.
vii. Broken Access Control
Broken access control is a silent invader of trust within your website. Imagine a locked door to sensitive customer data, but someone left the key lying around.
This vulnerability occurs when users can access resources or perform actions beyond their intended permissions. It’s like an unauthorized user sneaking past the velvet rope at a VIP event.

The consequences? Data breaches, exposure of confidential information, or even full control of the website landing in the wrong hands.
Moreover, this type of breach often goes unnoticed until it’s too late. Attackers leverage weaknesses like improper session handling, insecure direct object references (IDOR), or failure to enforce role-based permissions. Suddenly, your site’s admin panel is accessible to hackers, and they’re wreaking havoc.
viii. Security Misconfiguration
Think of security misconfiguration as leaving your front door open after installing a high-tech lock. Even the best systems crumble when configurations are sloppy or default settings remain untouched.
Misconfigurations—whether in servers, databases, or CMS platforms—are an open invitation for hackers.
Attackers actively scout for unpatched software, unnecessary features, or overly verbose error messages exposing internal details. For example, a misconfigured error page might reveal the structure of your database, serving as a treasure map for cybercriminals.
Don’t let a lazy setup be your Achilles’ heel. Regularly review and update your configurations, disable unnecessary services, and enforce least-privilege principles. A misconfigured website isn’t just a mistake—it’s a ticking time bomb waiting to explode.
ix. Insecure Website Hosting
Your hosting provider is the foundation of your website, but if it’s insecure, you’re building your digital home on quicksand. Insecure hosting services often fail to implement robust security measures like encryption, firewalls, and regular patching.
The result? Your site becomes a playground for attackers.

A compromised host can lead to server hijacking, malware injections, and widespread data breaches that tarnish your brand’s reputation. Worse, shared hosting plans amplify the risks—one vulnerable site on the server can act as a gateway for attackers to infiltrate yours.
To protect your website, choose a hosting provider that prioritizes security. Look for features like SSL certificates, DDoS protection, and frequent updates. Secure hosting isn’t just a service; it’s an investment in your website’s longevity and credibility.
x. Spamming
Spamming isn’t just an annoyance; it’s a gateway to malicious activity. From filling your contact forms with fake entries to flooding your comments section with links to shady sites, spammers aim to disrupt your website’s functionality and trustworthiness.
Worse, unchecked spam can hurt your SEO, lowering your search rankings and credibility.
Sophisticated spammers use bots to exploit vulnerabilities, such as weak CAPTCHA systems or poorly secured forms. Some even insert malicious links, tricking unsuspecting users into phishing scams or malware downloads. Your website isn’t just being spammed—it’s being weaponized against your visitors.
Combat spammers by employing robust CAPTCHA solutions, spam filters, and monitoring tools. Regularly update your website’s plugins and scripts to seal off potential entry points. Don’t let spammers dictate your website’s narrative—fight back and maintain your digital fortress.
Understanding the Website Security Framework
A website security framework determines how secure your website is. Even if you’re just starting out, developing a firm framework can help reduce security breaches.
The model for a good cybersecurity framework was first made by the US National Institute of Standards and Technology (NIST). This framework should be taken for reference while constructing your own.
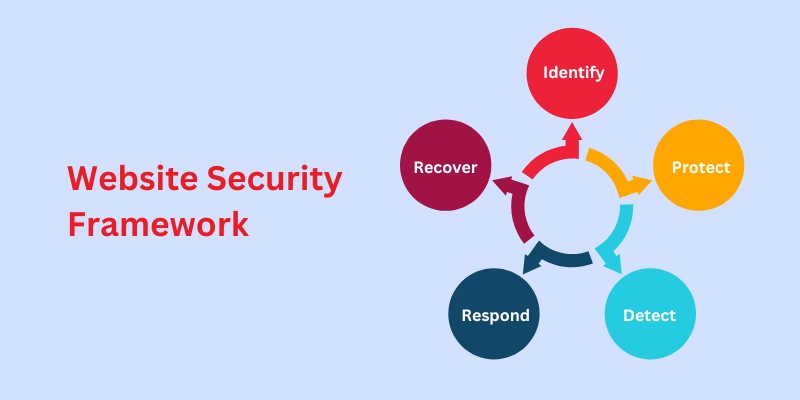
A security framework should be your foundation in making a secure website. But this framework isn’t really complete. Hence, you need to keep yourself updated about vulnerabilities and change the framework as required.
There are 5 stages of website security framework: identify, protect, detect, respond, and recover. Let’s see what each of them does.
i. Identify
During the identification stage, all the assets of a website are documented and reviewed. Assets of a website include web properties, servers, infrastructure, extensions, services, and access points.

This stage helps in identifying security threats in your website’s assets. You should take steps to solve any security vulnerabilities found during this process. We’ll be talking in detail about how to solve those security vulnerabilities throughout this article.
The identification stage is also one of the key steps in securing your website as it helps protect against XSS, DDoS, and ransomware attacks. You should execute this stage very seriously.
ii. Protect
After you’ve identified vulnerabilities in your website’s assets, it’s time to defend against future breaches. Protect stage helps you secure your website further by applying some preventive measures.

Now you might question if hackers can get in through anywhere, where do I begin? This isn’t what the Protect stage actually is. Protection can come from training your employees to be aware of phishing and ransomware attacks, apply two-factor authentication on login pages, and so on.
But, the best way to truly protect your website is by activating a web application firewall. Firewalls help in filtering unwanted traffic and malicious files, so they don’t get to your website.
Since security is a process, you should take the time to think of potential vulnerabilities and solve them. You can also hire a cybersecurity professional once every six months to test your website.
iii. Detect
The detect phase is when you’ve completed previous security checks and are now starting to actively monitor your website for vulnerabilities.

You might be confused about where to get started. We recommend you check your Domain Name Server (DNS) records for any malicious files lingering around. After the gateway to your website has been cleared, you can move on to web server configuration, application updates, user access, file integrity, website firewall, and so on.
If you can’t do this on your own, you can always hire a professional to do it for you. You can also use security tools like SiteCheck to scan for potential threats to your website.
iv. Respond
The Respond stage is when despite your security measures, you get attacked. This can happen as security is always evolving.
A response plan is always needed if your website ever gets attacked. Having a plan will also be very useful for future attacks. A proper response plan includes having a response team, reporting incidents to review findings, and tackling the issue.

The response stage is very broad. Firstly, to respond to an event, you’d need to be prepared and well-planned. You need to collect resources and use tools available to you to secure your website.
Then, you need to detect and analyze the threat. Next is containment or eradication. Meaning that you can either choose to make the vulnerability useless or destroy it completely.
But this comes with time. That’s because you’ll need to analyze a lot of vulnerabilities in order to be able to correctly contain or eradicate a threat. You need to be able to identify a threat at first. And then you’ll need to identify the type of threat. Then you can proceed to destroy it.
It’s a long process but an important one. You can’t leave threats unidentified or not dealt with on your website.
v. Recover
Recover stage is the final stage of the website security framework. It’s done after the completion of all the above stages. Recover also refers to backup plans in case you fail on any of the above stages.
The above stages may fail on strong ransomware attacks or large DDoS attacks. In these cases, having a backup of all your data will be of great help.

You can also minimize your chances of failing at previous stages through the recovery stage because this stage includes uploading your data on the cloud. Cloud is the best way to combat DDoS attacks.
That’s because the way cloud works is; it redirects the heavy traffic from DDoS attacks to other servers on its network. And since those servers don’t have your website’s DNS, a hacker won’t be able to access or shut down your website.
Something that also helps a lot is having an effective communication strategy. You need to communicate to your customers that a breach has occurred so they can also apply safety measures on their part to be safe.
Another is to use automatic backups. Every time you make changes on your website, it should be backed up automatically, so you don’t forget to do so. This also helps in case a hardware failure occurs.
You can also use backup tools such as Rsync backup, Cpanel backup, and even cloud backup to keep your website secure.
After everything we know up until now, let’s jump into what you’re truly here for. How to secure your website. If you scrolled all the way into this, we recommend you read from the very beginning because everything before this was crucial information you need in order to understand how to secure your website.
Let’s see how you can secure your website in the most effective manner.
Implementation of the CIA Guideline
Let’s look at the basic security guidelines that every website owner and organization must follow.
i. The CIA Triad
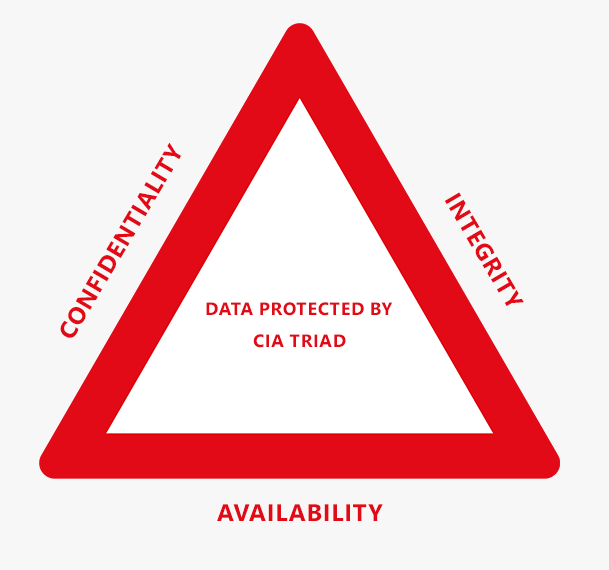
A method of testing your own security is the CIA Triad which is: Confidentiality, Integrity, and Availability. This model is the backbone of security on a website or an organization. It’s also a security check for secure websites just to be sure.
ii. Confidentiality
Confidentiality is the restriction of access to control of information for everyone in your organization. Only an authorized person may control the data of your organization.
For example, if your house can be opened with keys and you leave the keys at your door, anyone can get in. Confidentiality is like adding an extra layer of protection to your private space, be it adding multiple locks or even a fingerprint lock.
This helps in reducing risks of social engineering attacks, which we’ll get into later.
iii. Integrity
Integrity is the insurance that the receiver of data receives unaltered data. Your data can be altered during the transfer process by hackers. Your organization must be able to send and receive unaltered data.
For example, if a hacker were to interfere in your deal with a customer, the hacker could change the entire deal. That could be a loss for you.
iv. Availability
Availability is exactly as it sounds like. Access to data should be available to authorized personnel when needed. If your organization is compromised, a backup should be available instantly. This helps in reducing data leaks.
If your website or organization fulfills the triad, it’s secure at a basic level. Just know that those beginner hackers won’t be able to get into your website with this fulfilled.
Now that we have some basic understanding of why hackers would hack your website and a basic security check, let’s get into some potential vulnerabilities that may affect your website.
How to Secure a Website?
Now that you know how your website can be compromised, it’s time to actually secure your website. There are numerous ways to secure your website even after you’ve check-marked the CIA Triad.
Website security is something that you simply can’t overlook. Here are some effective ways to increase your website’s security.

i. Constant Updates
One of the major reasons why websites are compromised nowadays is due to outdated software. This may seem very obvious but updates are a vital part of your website’s security. You should update your website as soon as a new plugin or CMS version is available.

Most website attack vectors are automated. And updates most likely consist of a security patch that can stop those automated attacks. You should update your website as frequently as possible.
If you’re using a website builder, you don’t have to worry about updates as much. That’s because most website builders will handle your website’s security for you.
Check out the process to update WordPress to the latest version. Unsure how to check your WordPress version? Here’s the guide for that too!
ii. Firewall
Having constant updates isn’t quite enough to secure a website. You need something that can filter unnecessary traffic and malicious code that your website gets.
That’s a website firewall. Firewalls add an extra layer of security to your website by filtering unwanted information. Hackers can take your website down from your server or network using DDoS attacks. A firewall prevents that from happening.
If you used a website builder, firewalls are usually readily available. In any case, you should always contact your website builder to make sure you have firewall protection.
The recommended website firewall providers are Sucuri, Cloudflare, and SiteLock.
iii. Strong Passwords
We can’t stress enough how important strong passwords are for your website’s security. A secure website greatly depends upon your passwords. Having a username and password as admin/admin is pretty useless.

Databases of cracked passwords are readily available online for hackers to use. Most of those passwords are moderately strong to weak ones. So, having a strong password already puts you in a safe zone.
- The best way to have a strong password is to use unique passwords everywhere. If you’ve used one password somewhere, we recommend you don’t use that elsewhere.
- Another way to secure yourself is to have long passwords. If you have a long password, hackers will have a harder time figuring out your password.
- You can also use random passwords too. Since random passwords are very difficult to figure out by any means, using one adds an extra layer of security.
- There are a lot of password managers like LastPass through which you can use a random password and not forget it.
iv. Install SSL
Secure Sockets Layer (SSL) certificates encrypt data in between the host and the client. SSL certificates ensure that your data is reaching your clients without any hindrance in between.
SSLs also show who is sending the data to the receiver so that your clients know it’s your website. This also prevents hackers from using redirection to trick your clients.
However, SSL certificates don’t actually protect websites from cyberattacks. Their sole purpose is to encrypt your data so that nobody can interfere with it during the transmission process.
Check out the process to install an SSL certificate in our stepwise guide.
v. Reliable Backup
Backups are crucial in the event of a security breach. They help in recovering your files in case hackers modify or delete them. Backup shouldn’t be your only security option, but they do help in recovering your files.
But backups need to be reliable to be effective. For a reliable backup, you should have automatic backups enabled. This way, you don’t have to stress about backing up everything manually after you complete your work every day.
Second, your backups need to be off-site backups. Meaning that you need to keep your backup somewhere that is not on the same server as your website. This helps in various ways. If hackers target your website, they can’t destroy your backup, so you’ll be up in no time.
Off-site backups are a lifesaver in case of a hardware failure. If you have it on the same server as your website and a hardware failure occurs, you have no way to regain your files again.
When using WordPress, go with one of the best WordPress backup plugins. This includes UpdraftPlus, BackupBuddy, etc. Learn how to back up your website from this guide.

vi. Limit Access and Permissions
Hackers have a lot of ways to get into your website. One such way we talked about before is phishing. If they can’t get to your website through you, they’ll surely try to get in through your employees.
And that’s where the principle of least privilege comes in. According to this principle, a website should be able to use minimal privileges to execute an action and grant privileges to individuals only at the time of execution of the action.
This ensures that there is only one person with the highest privilege who can grant limited privileges to lower-ranking individuals. Privileges dictate what individuals can and can’t do. So, the highest privilege should always be granted to the most responsible person.
Hackers can manipulate your employees to gain access to your website if they have admin privileges. This can harm your website. So, limiting access and permissions is a must.
vii. Monitoring Tools
Monitoring tools are exactly what they sound like. They monitor your website constantly to check for unwanted activity. Monitoring tools can improve your response time and help you in damage control in case of a security breach.
Monitoring tools are most useful in the long term. When you have enough data from potential breaches, you can further secure your website. Months of logs can be useful to detect application malfunction as well.
Record and regularly review all actions that occur in the critical parts of the application, especially in the administration areas. Hackers could try to exploit a less expected part of the website to gain higher access later. Creating triggers to alert you in case of a security breach helps a lot as well.
Check about website maintenance and the best website maintenance services.
viii. Personal Security Practices
As a website owner, you should secure not only your website but your computer as well. Hackers may target your device to gain access to your website.
Remove all unused applications from your computer and scan for malware regularly to be safe from attacks. You should also have a computer password that is difficult to figure out.
Having unnecessary extensions can also harm your security. Extensions can have privacy issues that a hacker can exploit. Remove extensions you don’t need. Also, only install trusted extensions.
If you see an odd application on your computer, you can search it online to know what it does. If it doesn’t come up on searches, it’s most likely malware.
ix. Use Website Security Service
Website security services are tools that help to strengthen your website’s security. They check your website for malware, and provide you with search engine diagnostics and security reports.
There are many website security services on the internet. We recommend you use Sucuri security tools to secure your website as it’s one of the best and most trusted tools.
There are other security services such as the Open Web Application Security Project (OWASP), SANS Institute, and the National Institute of Standards and Technology (NIST).
They all provide security services so you can focus on your business. Whichever you plan on using, always remember to read their reviews first.
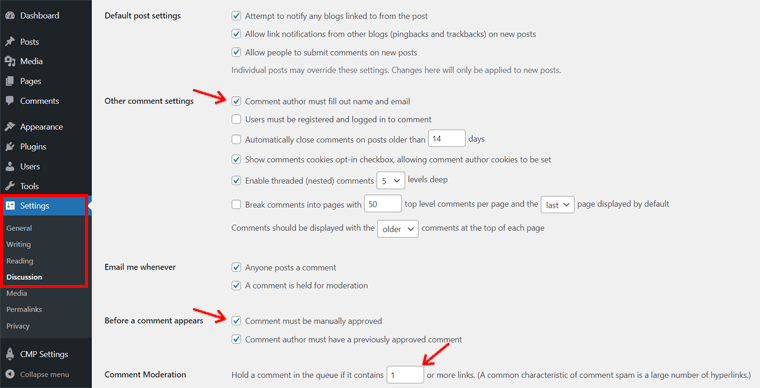
x. Proper Website Settings Configuration
Proper website settings configuration is the backbone of online security. A misconfigured website, such as one with default credentials or unnecessary permissions, is a goldmine for hackers.
By ensuring settings like file permissions, security headers, and database credentials are correctly configured, you close off common entry points for cyberattacks.
Regularly updating configurations and disabling features you don’t need—like directory indexing or default admin pages—adds an extra layer of defense.
Moreover, attention to settings such as HTTPS enforcement and session timeouts ensures your users’ data is transmitted securely and prevents unauthorized access. Combine this with proactive monitoring for anomalies, and your site is well on its way to becoming a security stronghold.
On a WordPress site, proper settings configuration means changing the default login URL, disabling XML-RPC if not in use, and enforcing strong passwords for all users.
xi. Use of Trustworthy Plugins and Add-ons
Plugins and add-ons can enhance website functionality, but they’re also a major target for cybercriminals. Using unverified or outdated plugins can introduce vulnerabilities, giving hackers a backdoor into your website.
Stick to trusted sources, like official repositories or premium developers with a track record of security. Always check for reviews, updates, and compatibility before installing.
Keep in mind that even reputable plugins can become risky if left unmaintained. Schedule regular updates and remove inactive or unused plugins to minimize your attack surface.
Use plugins like Wordfence or Sucuri Security to monitor and enhance protection.

For plugins and add-ons, stick to reputable ones from the WordPress repository. This involves Rank Math for SEO and Elementor for page builder, and always keep them updated.
xii. WHOIS Protection
WHOIS protection is your first line of defense against privacy-related attacks. Without it, your domain registration details—like name, email, phone number, and address—are publicly available.
As a result, this makes you a target for spammers, phishing attacks, and social engineering schemes. WHOIS protection anonymizes this information, shielding your identity and preventing unnecessary exposure.
Beyond personal privacy, protecting domain details also makes it harder for hackers to study your website’s infrastructure. Many registrars offer WHOIS protection as an add-on, and it’s a small investment that pays off big in terms of security.
WHOIS protection comes into play when registering your domain. Services like Namecheap and GoDaddy offer this as an add-on to keep your registration details private.

xiii. Utilize a Secure Website Hosting
Secure hosting is the foundation of a protected website. A reliable hosting provider should offer features like SSL certificates, daily backups, DDoS protection, and server firewalls.
Beyond features, the hosting infrastructure itself should be regularly patched and monitored for vulnerabilities. Shared hosting, while economical, can expose your site to risks if other hosted websites are compromised.
Investing in a hosting provider that prioritizes security ensures you’re less susceptible to breaches, malware injections, or server hijacking. Whether it’s VPS hosting or managed WordPress hosting, opt for a solution that fits your security needs without compromising performance.
Secure hosting from providers like Hostinger, SiteGround, or Bluehost ensures advanced features like automatic updates, malware scans, and DDoS protection.

3+ Best Free Website Security Checking Tools
Regularly monitoring your website for security vulnerabilities is crucial to ensuring its safety. Identifying weak points and keeping your site updated is key to staying ahead of potential threats and safeguarding your data.
Luckily, several online tools allow you to test your website’s security at no cost. Here, we’ll introduce you to some of the top free tools for checking and enhancing your website’s security.
1. Patchstack
Patchstack stands out as a specialized security tool designed to protect websites, particularly WordPress. What sets it apart is its real-time vulnerability detection and virtual patching system, which continuously monitors your site for outdated or risky plugins and themes.
Instead of waiting for developers to issue updates, Patchstack provides temporary security patches, so that your site remains secure even against zero-day exploits.
Another unique feature is its community-driven database, where security experts contribute information on vulnerabilities. Its developer-friendly approach also allows integration with custom plugins, making it perfect for advanced users and agencies.
2. Wordfence Security
Wordfence Security is a powerhouse in website protection that offers an industry-leading web application firewall (WAF) specifically designed for WordPress. Its real-time IP blocking feature uniquely identifies and blocks malicious traffic from even reaching your website.

Unlike other tools, Wordfence also provides a detailed audit log, helping you trace suspicious activities and pinpoint potential vulnerabilities with precision.
What truly sets Wordfence apart is its machine learning-driven malware scanner, capable of detecting backdoors, phishing attempts, and malicious redirects. The live traffic view allows you to monitor activity in real time, giving you complete control over who’s accessing your site.
3. Sucuri Site Checker
Sucuri’s Site Checker is a go-to tool for quick, reliable website scans. It checks your site for malware, blacklisting, injected spam, and malicious code with unmatched speed and precision.
Unlike many other tools, Sucuri provides a public malware report, making it easy to analyze and share vulnerabilities. Its Blacklist Monitoring feature is particularly impressive, ensuring your site isn’t flagged by search engines or security services.
Sucuri also offers unique post-hack cleanup services, making it ideal for recovering from cyberattacks. Paired with its robust firewall and continuous monitoring, Sucuri goes beyond basic security checks to offer a comprehensive defense against threats.
4. MalCare
MalCare is not your typical security tool—it’s an all-in-one solution with a focus on malware prevention and removal. What sets MalCare apart is its one-click malware removal, which cleans your site without affecting functionality.
Unlike tools that rely solely on signature-based detection, MalCare uses heuristic scanning to identify new and unknown threats proactively.
Another standout feature is its automatic daily scans that ensure your site stays protected even when you’re not actively monitoring it. MalCare also integrates with WordPress for seamless setup and comes with a built-in staging environment.
Conclusion
In this article, we went through what website security is and what can compromise your website’s security. We also talked about how to deal with potential vulnerabilities and went through some security measures that you can apply to keep your website safe.
If you have any queries or suggestions feel free to comment below in the comment section.
We hope this article helped you to learn about website security. You might also want to see articles on how to remove ‘not secure’ from your website and the best web hosting companies.
And if you liked this article, do share it with your friends and colleagues. If you’d like to, follow us on Facebook and Twitter for more articles like these.
References
- [1] https://securitytoday.com/articles/2023/07/31/report-67-percent-of-businesses-lack-confidence-of-full-recovery-after-cyber-attack.aspx
- [2] https://www.statista.com/statistics/873097/malware-attacks-per-year-worldwide/
- [3] https://www.statista.com/statistics/653688/distribution-of-mobile-malware-type/
- [4] https://www.statista.com/statistics/494947/ransomware-attempts-per-year-worldwide/